Security is the key
June 3, 2019, 8:50 a.m.
Author: Robert Plestenjak (XLAB)
Intrusion Detection (ID) SEE is a security appliance built for the M2DC platform, performing real-time network traffic inspection. With a web-based user interface, integrated into the M2DC middle-ware, it provides insight into incoming and outgoing network traffic.
With different rules, it can enforce corporate policies, raise and alert when harmful web pages or applications are accessed, and it can even actively block them if so configured. The ID_SEE is not a firewall, but provides an additional layer of security.
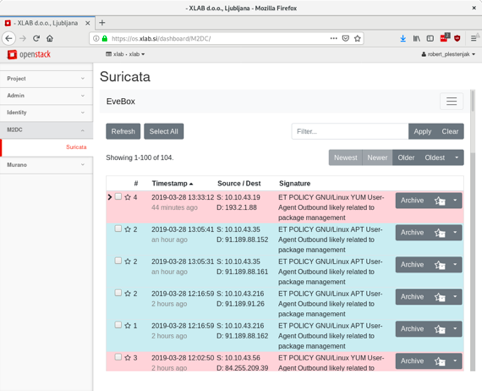
Figure 1: Screenshot of the ID_SEE list of security events
Overview and general characteristics
In the context of M2DC, the ID_SEE deploy utilizes available hardware acceleration of the high-performance Intel CPU based server technology for very high throughput. On the other hand, it can use low power, highly parallel ARM platform for possible greater power efficiency.
ID_SEE deploy is using a Intel Hyperscan high-performance multiple regex matching library for high-throughput network environments. By utilizing CPU based acceleration, it greatly increases performance and with it, energy efficiency. With highly parallel architecture, it can also run on a low power ARM-based micro-server infrastructure, providing similar performance to higher-performant, but lower CPU core count Intel Xeon based micro-servers.
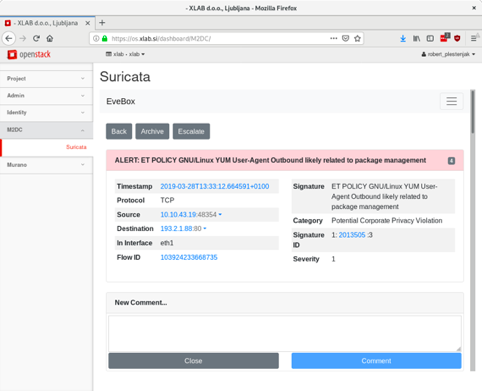
Figure 2: ID_SEE Security event, displaying part of the detailed information
Design
Network traffic is passed through the ID_SEE which can decode network packets and performs reg-ex based rule match on reassembled network streams. This is done in a highly parallel way using mulch-threaded approach, which greatly benefits from a number of available CPU cores. Because of low latency requirements, the appliance is limited to a single server for processing network traffic. Additional servers can be used for storage and user interface. Depending on the amount of network speed and traffic, different server architectures can be used. For absolutely highest throughput, server equipped with high-performance Intel Xeon CPU with high CPU clock and a large number of CPU cores is the best choice.
ID_SEE stores all the data in Elasticsearch database, which can be deployed on the same server or any other available server. The user interface is integrated into M2DC middle-ware, so plugin must be deployed on a middle-ware server. The appliance also deploys open source Suricata IDS security rules and keeps them up to date. Whenever one of the rules is matched, a security event is displayed. Each event can be examined in detail, including export in PCAP file, which can then be imported into specialized network analyzing tools (e.g., Wireshark, https://www.wireshark.org/). Besides security events, ID_SEE also provides various network traffic related reports like SSH connections, Net-flow, DNS query's, etc.
Network settings and connections also need to be configured. For Intrusion Detection case (ID), the best way to gather network traffic is via monitoring port on the network switch. All the traffic that is passing the switch up-link port, is simply mirrored to monitoring the port, which is then connected to one of the ID_SEE network ports. In the case of Intrusion Prevention setup (IP), the network traffic needs to be routed through ID_SEE server, so that ID_SEE appliance can actively block offending traffic.
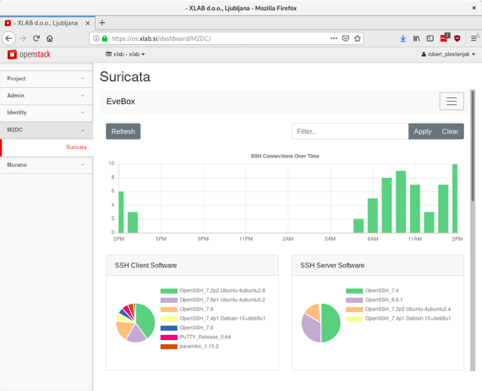
Figure 3: ID_SEE Report for SSH connections, including a selection of analytics.
Benchmarking
The ID_SEE is deployed with flexible Ansible automation tool. During deploy, various components are optimized for a target server architecture. Inclusion of Intel's Hyperscan library is automatic on Intel Xeon servers. The deploy provides a convenient and flexible set of instructions that greatly simplify installation. Performance wise, ID_SEE was tested on Intel Xeon CPU based server architecture and ARM server grade CPU based. Findings were presented in the public deliverable D5.4 – Hardware and Application Bench-marking. The final bench-marking results, together with power efficiency measurements will be published in the final benchmark delivery D5.5, also public and soon available at http://bit.ly/2W8TFDF.